
by Tataye
Written in Delphi
Released in August 2004
Made in Rumania




Beast 2.07 - Remote Administration Tool (AKA trojan)
- coded by tataye
Before using this program is STRONGLY RECOMMENDED to read
the help within the executable (BeastStuff/Help).
What's new:
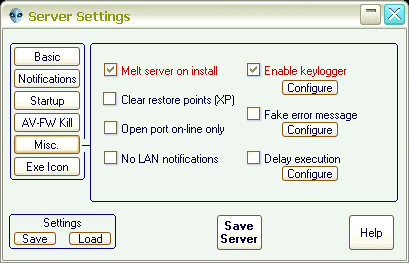
- keylog emailer
- smart keylogger
- live keylogger
- full skin support
- editable SMTP addresses
- Trillian passwords support
- Fun (Restrictions, CrazyMouse)
- smaller binder stub (5KB)
- more GUI options
- editable start-up keys
- remote Screen right click
- FileManager (queue downloads, column sorting, cancel downloads etc.)
- remote screen right click
- better port handling (not all ports open)
- etc.
Fixes/improvements:
- password finder works with injection
- time functions (delay execution, user time etc.)
- email notification
- ICQ notification
- SIN errors
- binder
- security hole
- more stability for both client and server
- closing the FileMangar while downloading/uploading
- and many more
Important:
- Beast 2.07 isn't compatible with the previous versions
- on a machine is allowed only 1 beast server, doesn't matter what version
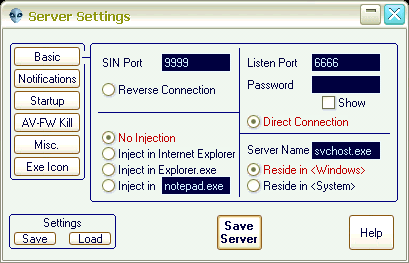
- if the reverse connection is enabled then SIN is automatically enabled (and vice versa)
- SIN can be used ONLY with reverse connection
Tataye
Server:
dropped files:
c:\WINDOWS\COMMAND.PIF size: 967 bytes
c:\WINDOWS\svchost.exe size: 30.869 bytes
c:\WINDOWS\COMMAND\msroem.com size: 30.869 bytes
c:\WINDOWS\SYSTEM\mslg.blf size: 227 bytes
c:\WINDOWS\SYSTEM\msludr.com size: 30.869 bytes
port: 6666 TCP
startup:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "COM Service"
data: C:\WINDOWS\COMMAND\msroem.com
HKEY_LOCAL_MACHINE\Software\Microsoft\Active Setup\Installed Components\{42CE4021-DE03-E3CC-EA32-40BB12E6015D} "StubPath"
data: C:\WINDOWS\SYSTEM\msludr.com
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run "COM Service"
data: C:\WINDOWS\COMMAND\msroem.com
MegaSecurity