by porno-sonic
Written in Visual Basic
Released in May 2003

=========================================================
- CODE INJECTION DOWNLOADER -
=========================================================
This is a test release of a VB6 web downloader that uses
interprocess memory injection on windows 2000 and XP.
(similar to the injection process that BO2K used, and others
later termed as "firewall bypass")
This serves 2 purposes:
- The program does not show up in the active process list
- The program will ask for internet access under the name
of the program it was injected into rather than it's own.
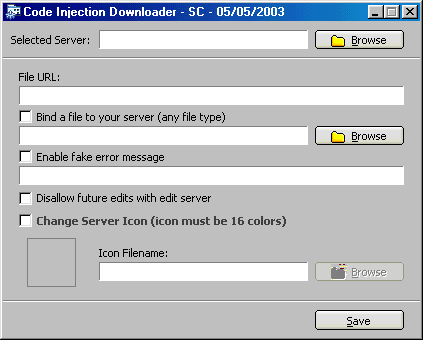
When executed, the server:
- displays a fake error message (optional)
- extracts and runs bound file (optional)
- disable Norton and McAfee AV (2000 and XP)
- attempts to inject into Kazaa (2000 and XP)
- If Kazaa is not running, it then injects into explorer
- The server then downloads the remote file, renames it
to .exe and executes it.
- Delete's itself from disk (continues to run in memory.)
- on 9x boxes, it hides from the tasklist by registering
itself as a service, downloads, runs, and ends.
- To end the the process on 2000/XP just close Kazaa or
explorer (depending on where it was injected)
porno-sonic
Server:
size: 8.767 bytes
startup:
none
added:
HKEY_CURRENT_USER\Software\VB and VBA Program Settings\winmedia\access
MegaSecurity