by All3GrO
Written in Visual Basic, Source included
Released in April 2001

CyberJack v1.00 - 21 March 2001
-------------------------------
Current Release: Server v1.01
Client v1.00
This is my first backdoor I've coded.
Cyberjack is developed using Visual Basic
and therefore, it requires VB6 runtime
files in order to work.
In addition, both the server and client
needs the Winsock ActiveX control, mswinsck.ocx.
Package contents:
RELEASE Folder:
- Exotic.exe (The CyberJack Backdoor Server)
- CyberJack.exe (The CyberJack Backdoor Client)
- Uninstaller.exe (The CyberJack Backdoor Server Uninstaller)
- Readme.txt (Some documentations)
SRC Folder:
- Client Folder (Full source code for CyberJack Backdoor Client)
- Server Folder (Full source code for CyberJack Backdoor Server)
- Uninstaller Folder (Full source code for CyberJack Backdoor Server Uninstaller)
Changes in Server version 1.01:
- Fixed system lock bug which causes system tray to be visible on some computers.
- Added Beep feature.
System Requirements:
- Intel Pentium processor or later (Pentium II or later recommended)
- 8 MB RAM
- 200 Kb hard disk space
- Windows 95/98/98SE/ME/NT/2000
- TCP/IP stack
- Network connection (LAN or Internet)
Note: CyberJack works best in Win9x systems. However,
when running on WinNT and Win2K systems, some functions will not work.
CyberJack is tested to run ideally on LAN/intranet environment.
It is not tested to run on Internet based WAN environment.
Instructions:
Give the server to the victim.
All the victim needs to do is to run the server and it will auto-install by itself
The server will be activated the next time the computer reboots and will remain in memory.
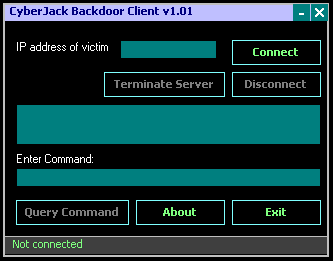
Once the server is activated, fire up the client and enter
the victim's IP address and click Connect.
When connected, you can have fun and play around with the functions.
Commands are provided by the server.
Click Query Command to view the list of commands the server supports
CyberJack Functions:
- Query all commands the current server supports
- Remote server termination
- Crash Win9x using the "con con" exploit
- Crash Win9x using DisableOEMLayer exploit
- Force shutdown Windows
- Open CD ROM tray
- Close CD ROM tray
- Loop CD ROM tray open & close
- Disable mouse
- Disable keyboard
- Disable CTRL-ALT-DEL
- Enable CTRL-ALT-DEL
- Hide system tray
- show system tray
- Hide system clock
- show system clock
- Hide start button
- Show start button
- Show control panel
- show display panel
- Get system info
- Send message
- Run program
- Website redirect
- Delete file
- Create directory
- Remove directory
- Hog system memory
- Lock computer
- Unlock computer
- Chat session
- Enumerate all running processes
- Retrieve all cached passwords including Dial-Up RAS passwords
- Beeps on victim's computer
Allegro
Server:
C:\WINDOWS\SYSTEM\Kernel32.exe
size: 69.632 bytes
port: 6789 TCP
startup:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run "Kernel32"
MegaSecurity