by ISO
Proxy, detected as "Backdoor" by KAV
Written in Visual Basic
Released in December 2000

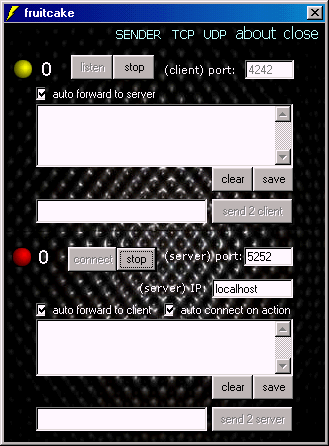
Its kind of a Trojan Proxy. No big deal, it just listens on a pre defined port, and makes a connection to another port. All Data that is transferred will be visible in text boxes. You might now ask, so what is it useful for? You can use it to have it act as a proxy between a Trojan Client and its Server. That means that you will see all the commands that are sent from the client to the Server and vice versa all answers from the Server to the Client. This can be used to study the Trojan functions or to make a list of the commands the client uses. Most Trojans could be used with Telnet as a client if you would know the right commands ISO size: 520.192 bytesMegaSecurity