by Alch3mizt
Written in Visual Basic
Released in september 2003


Fwb Dloader Beta uses a different method for bypassing firewalls than most fwb downwloaders
Most inject a dll into a process. Well thats kinda hard in vb so i had to improvise
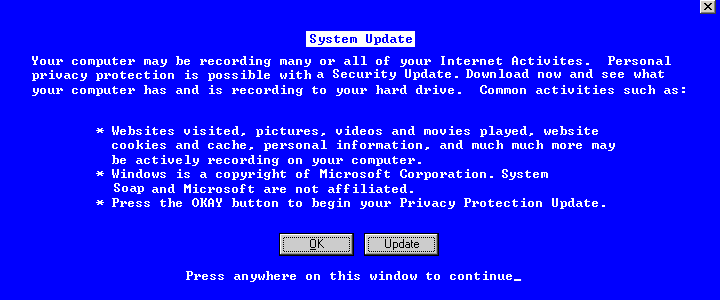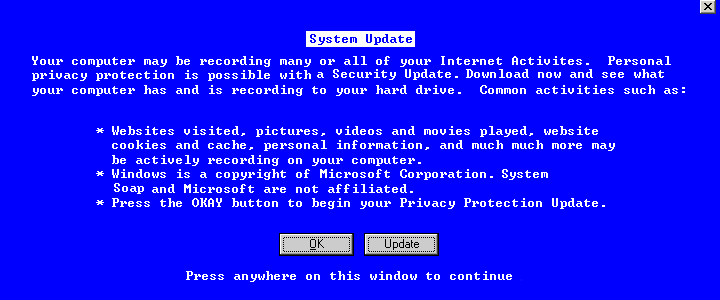
How it works. It is attaches to internet explorer as an activex control.
Everytime IE and/or explorer.exe is loaded the activex gets loaded aswell,
tricking the firewall into thinking IE is downloading the file.
So if the file it downloads is missing it will re-download the file everytime IE or
explorer.exe is loaded, disabling the need for a startup method :P
Its still beta but i hope to add it in CIA, watch this it will be memory resident once
you execute it so test it with something harmless!!!
Alch3mizt
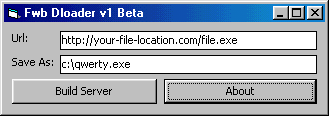
Server:
size: 11.857 bytes
file added:
c:\WINDOWS\SYSTEM\Fwload.dll
registry added:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Streams\88
HKEY_CURRENT_USER\Software\VB and VBA Program Settings
HKEY_CLASSES_ROOT\CLSID\{D1E0E395-612B-44A4-91A2-4093185ED7FE}
HKEY_CLASSES_ROOT\CLSID\{D5DE8D20-5BB8-11D1-A1E3-00A0C90F2731}
HKEY_CLASSES_ROOT\Fwload.ClsLoader
HKEY_CLASSES_ROOT\Interface\{18309C22-868D-46AB-953E-429769038EFF}
HKEY_CLASSES_ROOT\Interface\{4495AD01-C993-11D1-A3E4-00A0C90AEA82}
HKEY_CLASSES_ROOT\Interface\{737361EC-467F-11D1-810F-0000F87557AA}
HKEY_CLASSES_ROOT\Interface\{7500A6BA-EB65-11D1-938D-0000F87557C9}
HKEY_CLASSES_ROOT\Interface\{8284B8A2-A8A8-11D1-A3D2-00A0C90AEA82}
HKEY_CLASSES_ROOT\Interface\{83C49FF0-B294-11D0-9488-00A0C91110ED}
HKEY_CLASSES_ROOT\Interface\{C4D651F0-7697-11D1-A1E9-00A0C90F2731}
HKEY_CLASSES_ROOT\Interface\{C4D651F1-7697-11D1-A1E9-00A0C90F2731}
HKEY_CLASSES_ROOT\Interface\{C4D651F2-7697-11D1-A1E9-00A0C90F2731}
HKEY_CLASSES_ROOT\Interface\{CBB76011-C508-11D1-A3E3-00A0C90AEA82}
HKEY_CLASSES_ROOT\Interface\{E43FD401-8715-11D1-98E7-00A0C9702442}
HKEY_CLASSES_ROOT\Interface\{EB41E8C1-4442-11D1-8906-00A0C9110049}
HKEY_CLASSES_ROOT\Interface\{EB41E8C2-4442-11D1-8906-00A0C9110049}
HKEY_CLASSES_ROOT\Interface\{EB41E8C3-4442-11D1-8906-00A0C9110049}
HKEY_CLASSES_ROOT\Interface\{EB41E8C4-4442-11D1-8906-00A0C9110049}
HKEY_CLASSES_ROOT\Interface\{EB41E8C5-4442-11D1-8906-00A0C9110049}
HKEY_CLASSES_ROOT\Interface\{FCFB3D2B-A0FA-1068-A738-08002B3371B5}
HKEY_CLASSES_ROOT\TypeLib\{000204EF-0000-0000-C000-000000000046}\6.0
HKEY_CLASSES_ROOT\TypeLib\{8D427764-B798-4BF3-B6DC-A18187CE7050}
HKEY_CLASSES_ROOT\TypeLib\{EA544A21-C82D-11D1-A3E4-00A0C90AEA82}
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\explorer\Browser Helper Objects
MegaSecurity